Workshop
- Identity provider
- WARP and device posture
- Cloudflare Tunnel
- Access and Private Network
- Browser isolation and App launcher
- Digital experience monitoring
Now that we have an Identity Provider configured, we’re going to use it to enroll a user with a WARP client
First, let’s define who can connect devices to your organization.
[email protected]
On your lab Win11 VM, open the preinstalled WARP client and select Preferences:
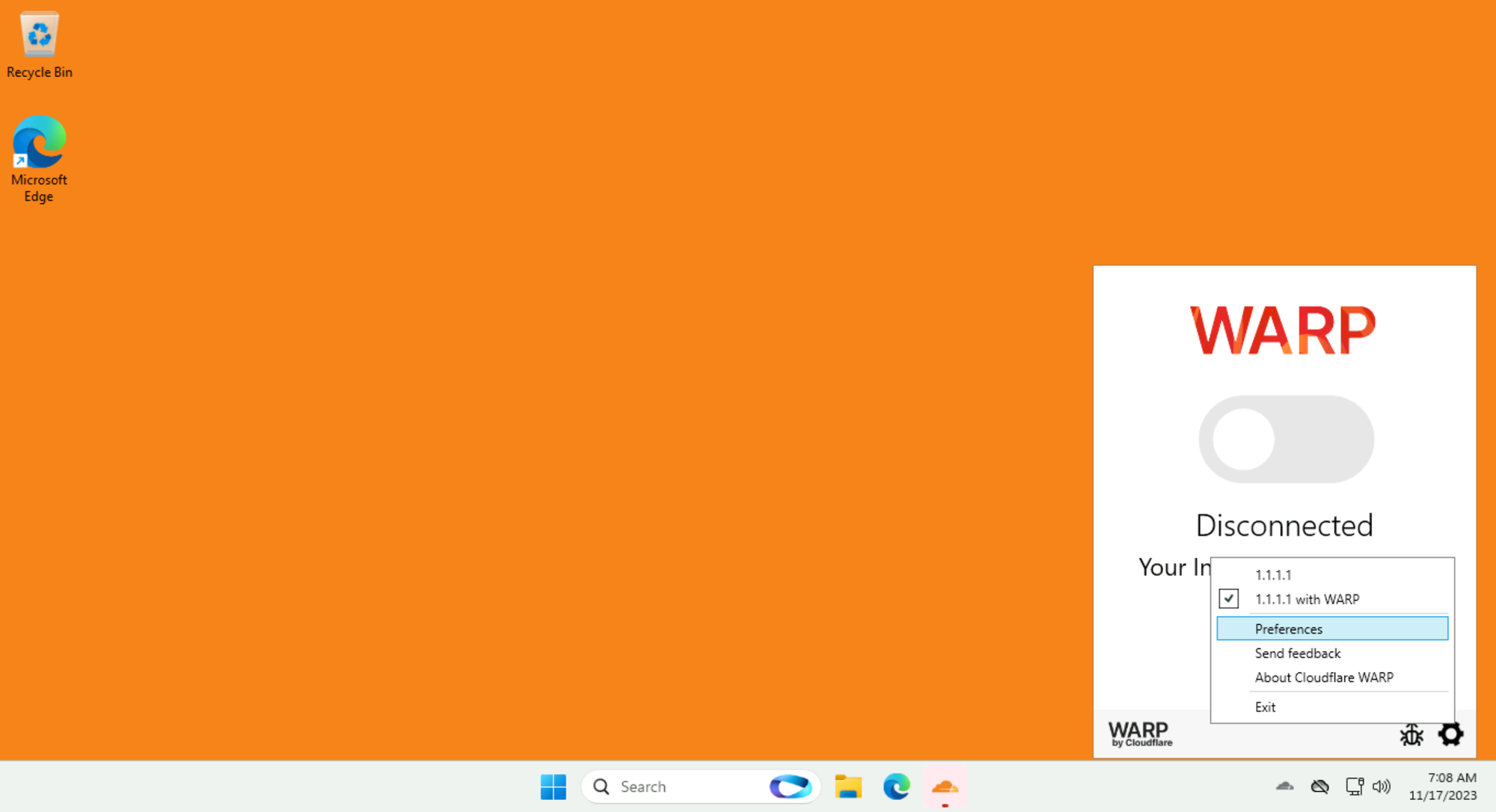
Then Account ‣ Login to Cloudflare Zero Trust:
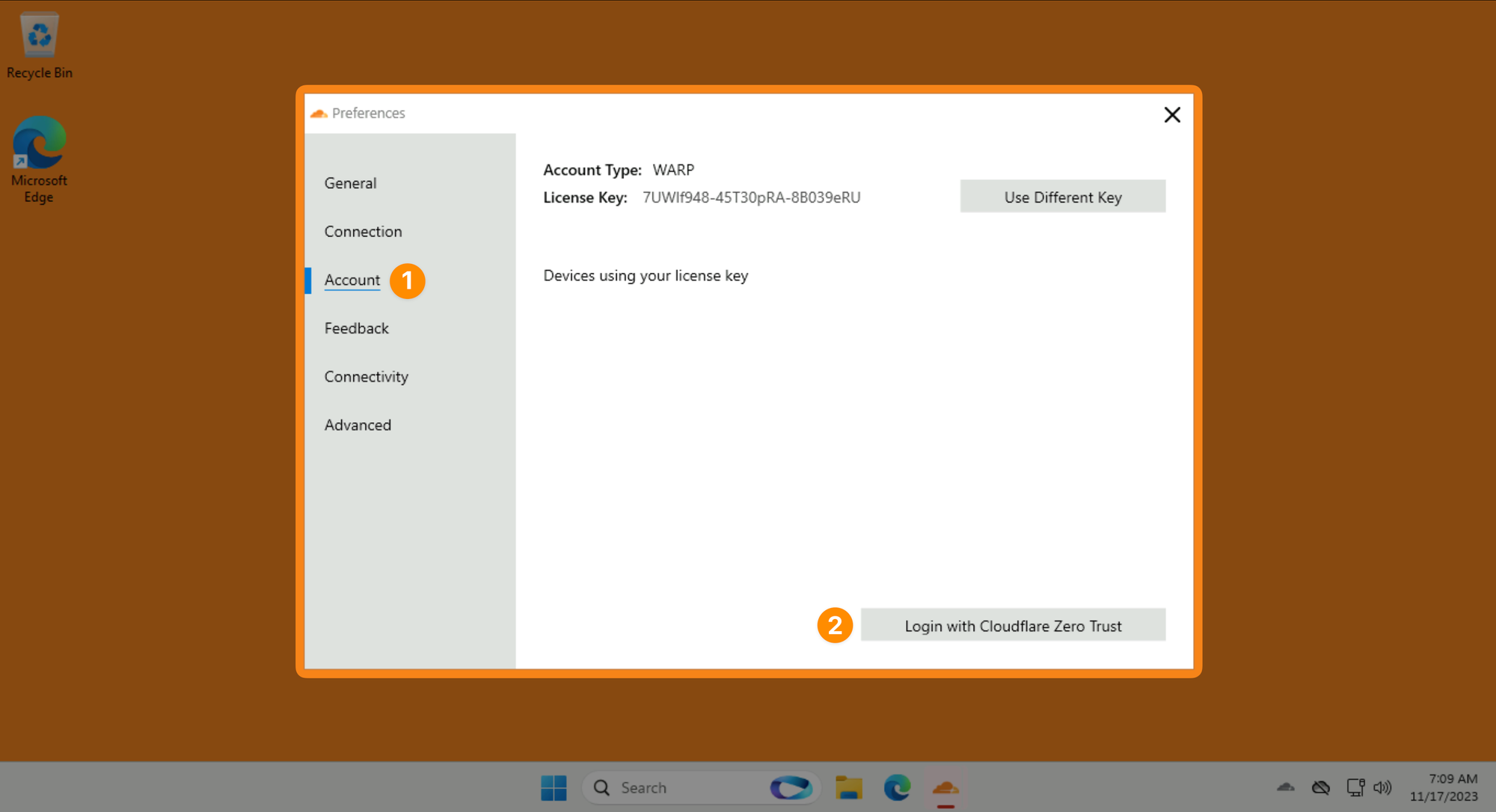
Use your LAB_SLUG when asked for a team name:
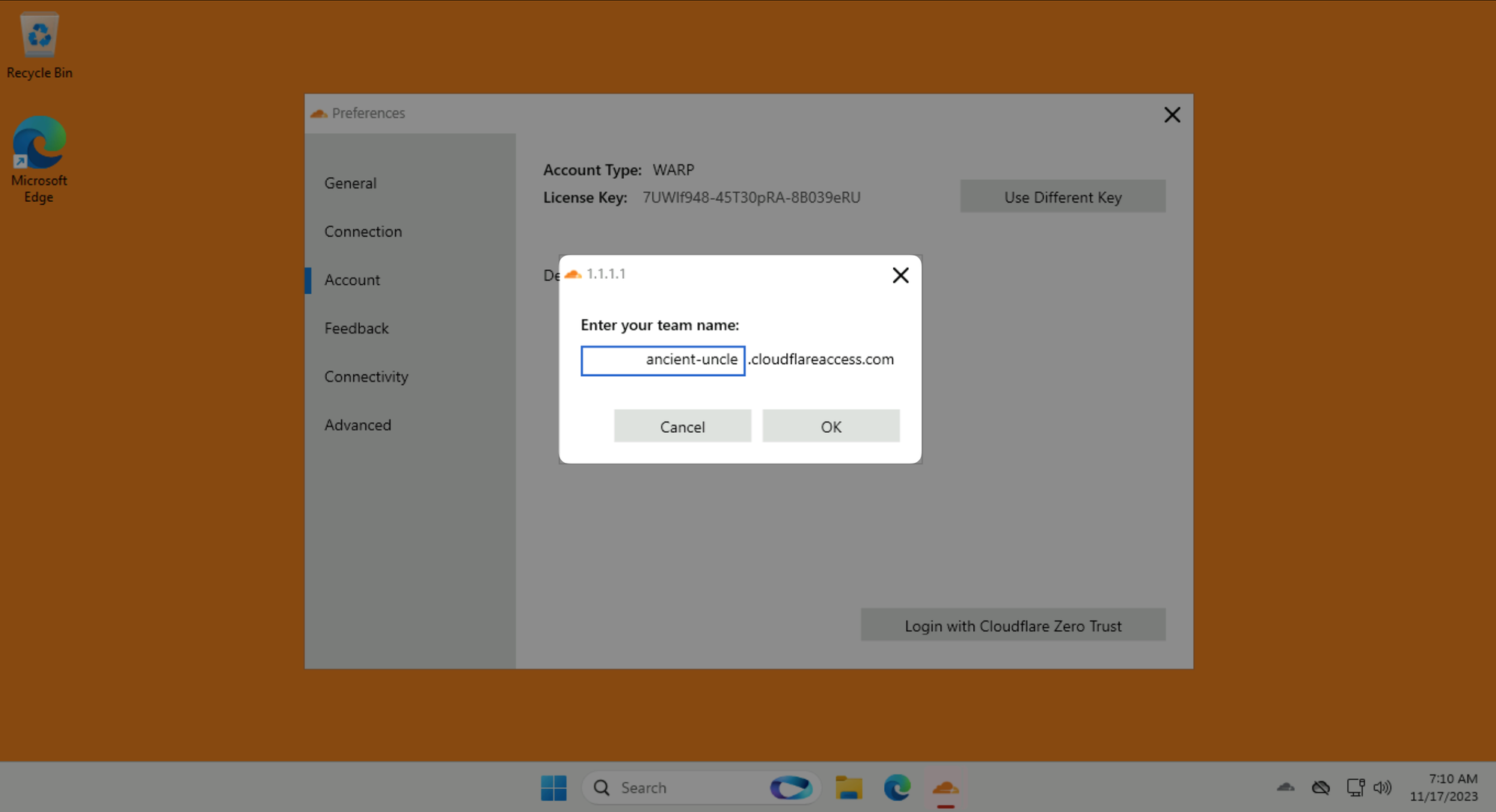
Click on Sign in with: SAML and log in as [email protected] with password #Savetheinternet.
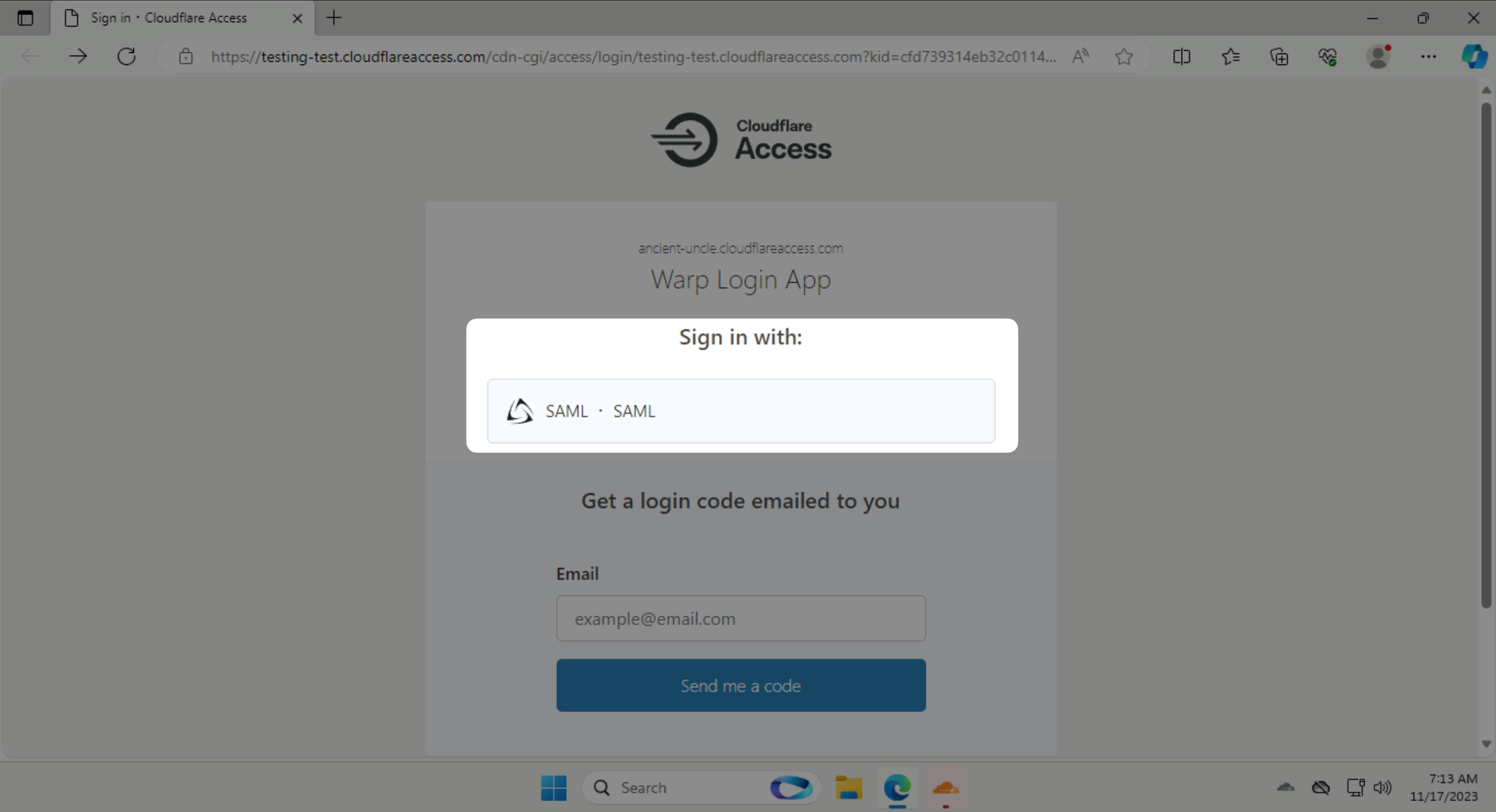
Once you are authenticated, click on the big grey button in the WARP client to connect to Cloudflare's network.
Once connected, your Zero Trust WARP client should turn blue:

Next, we’re going to use WARP to harden our device posture. You can configure Zero Trust policies that rely on additional signals from the WARP client or from third-party endpoint security providers. When device posture checks are configured, users can only connect to a protected application or network resource if they have a compliant and healthy device.
WARP tests on client machines fall into two categories:
Let’s create a device posture rule that checks if Notepad is running:
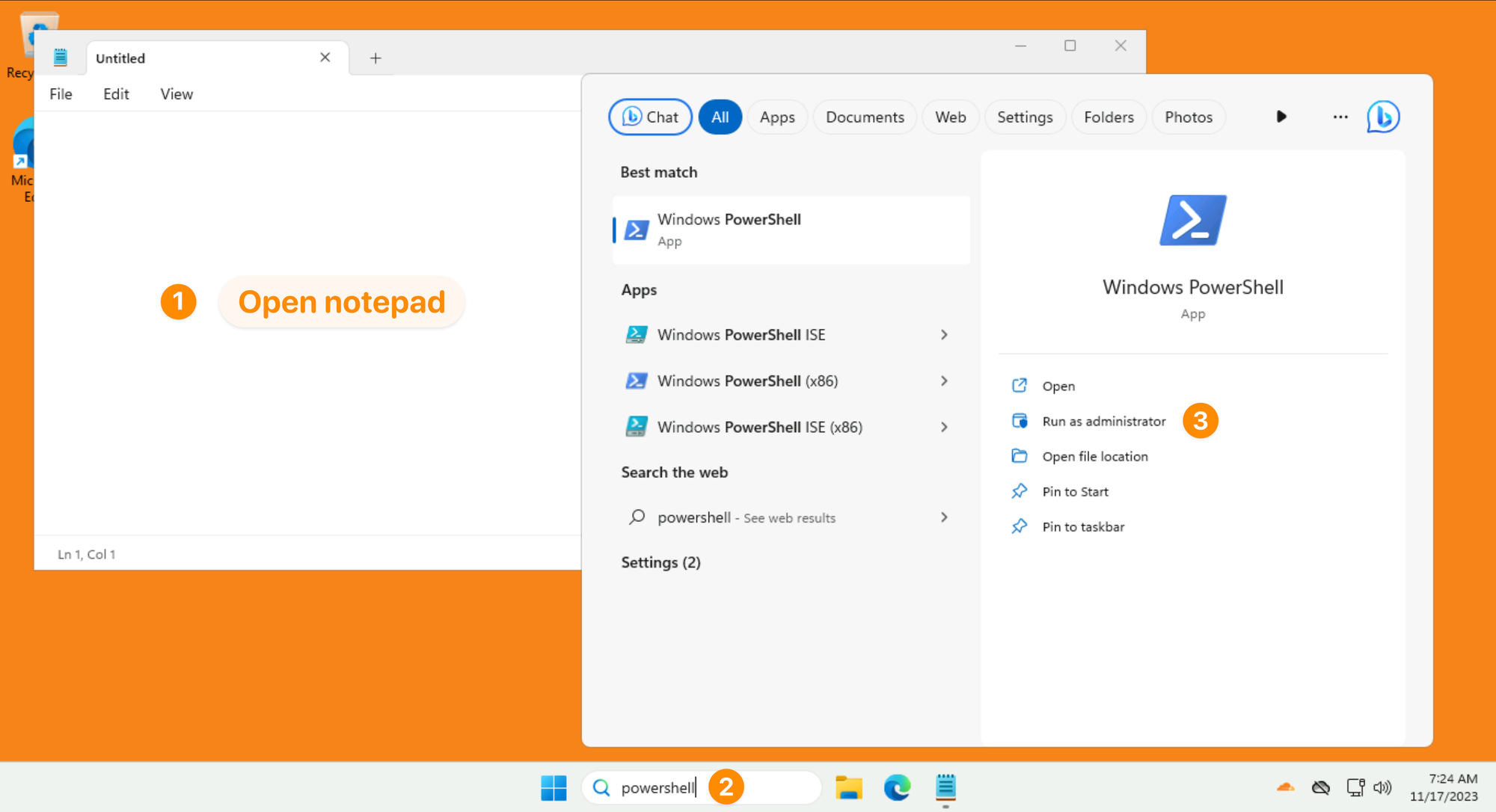
Paste this command in PowerShell:
Get-Process -Name Notepad | ForEach-Object {$_.Path -replace "\\","/"}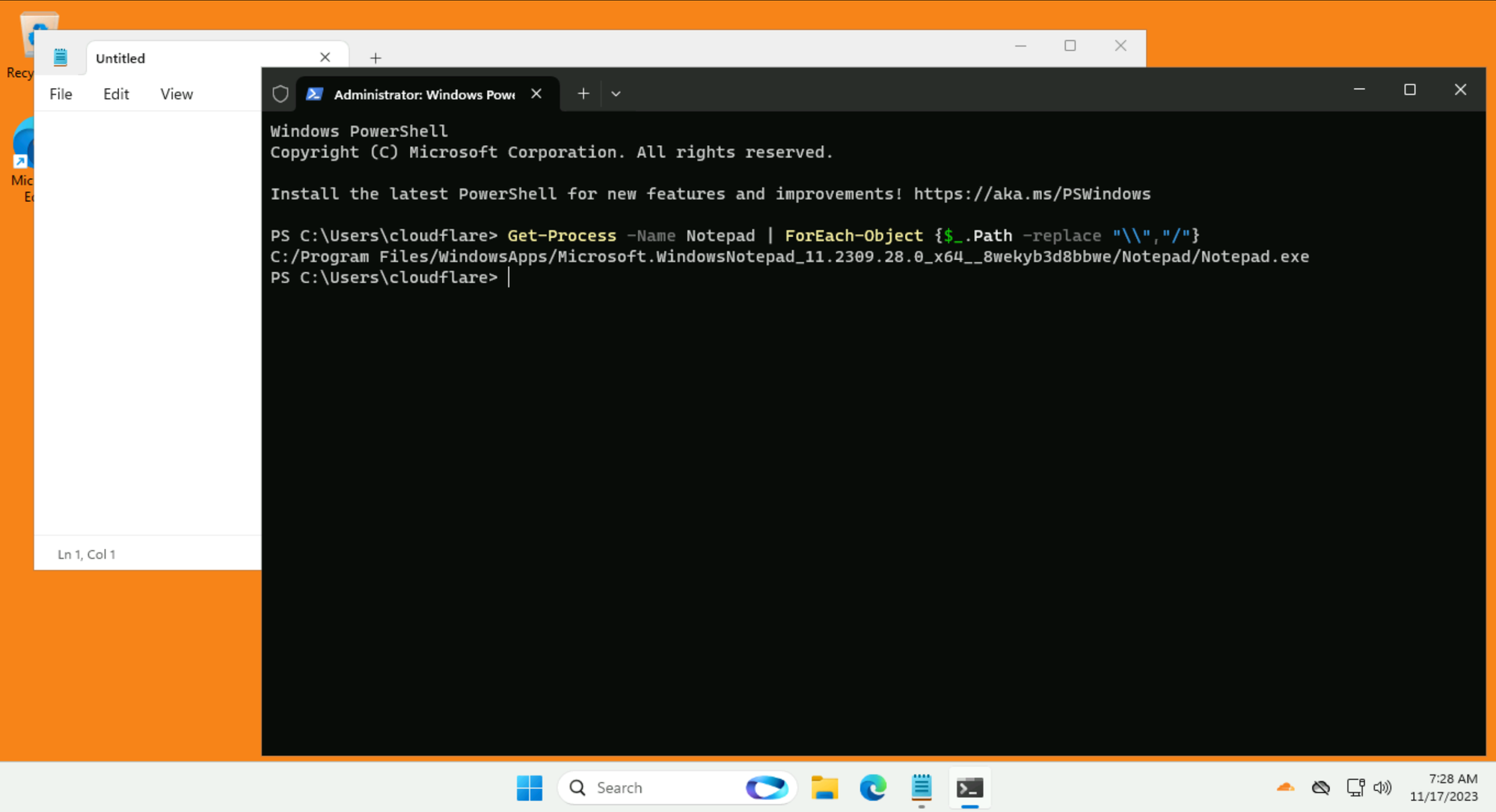
The output will look something like this: C:/Program Files/WindowsApps/Microsoft.WindowsNotepad_xxxx_x64__xxxxxx/Notepad/Notepad.exe
Copy this full path.
Next, return to the Zero Trust dashboard. Go to Settings ‣ WARP Client

Name: Notepad check
Operating system: Windows
Application path: <paste in the path you got from PowerShell>
Cloudflare polls the WARP client every 5 minutes to ensure the device posture requirements are met. If the client isn’t adhering to the device posture rules, authorization can be revoked.
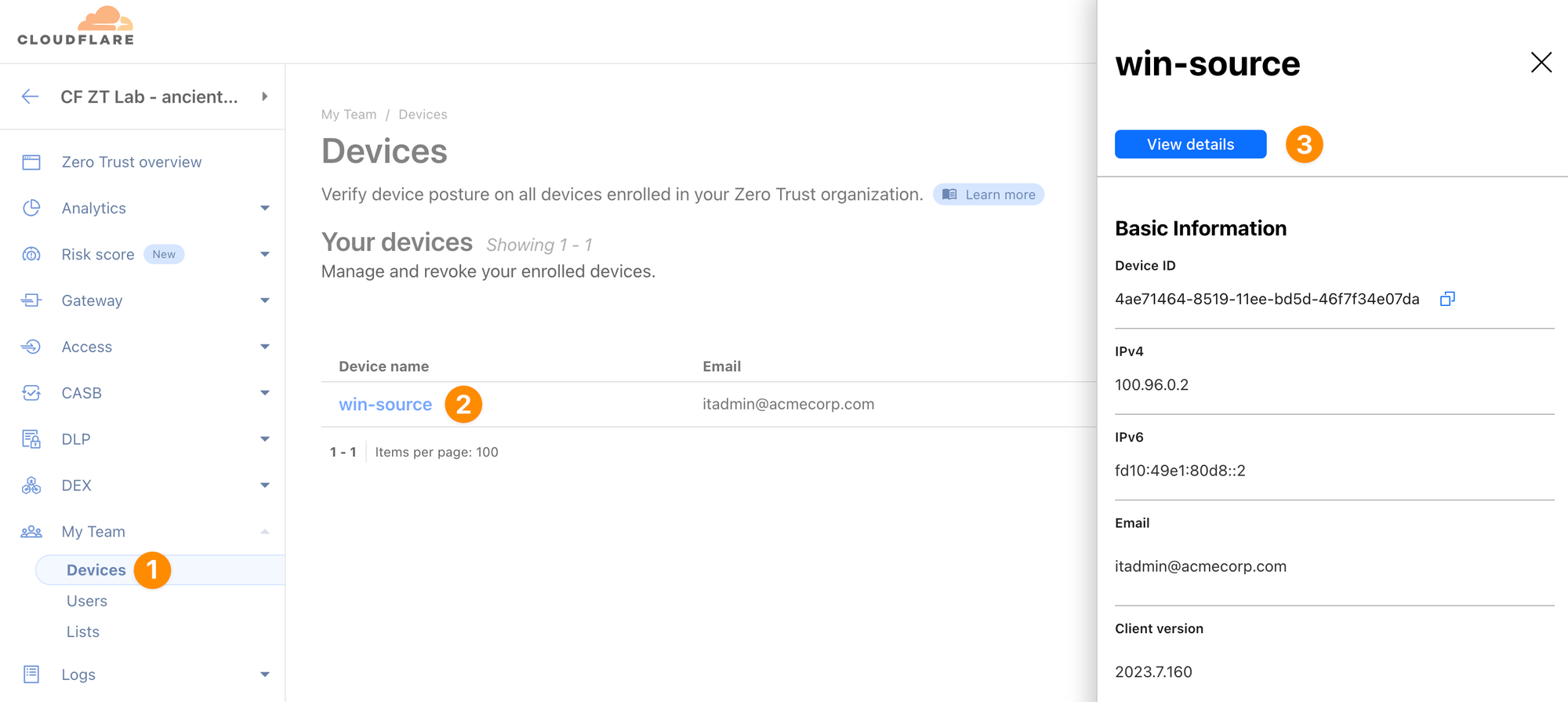
You can see how Cloudflare evaluates current status of a specific device in the dashboard under My Team ‣ Devices.
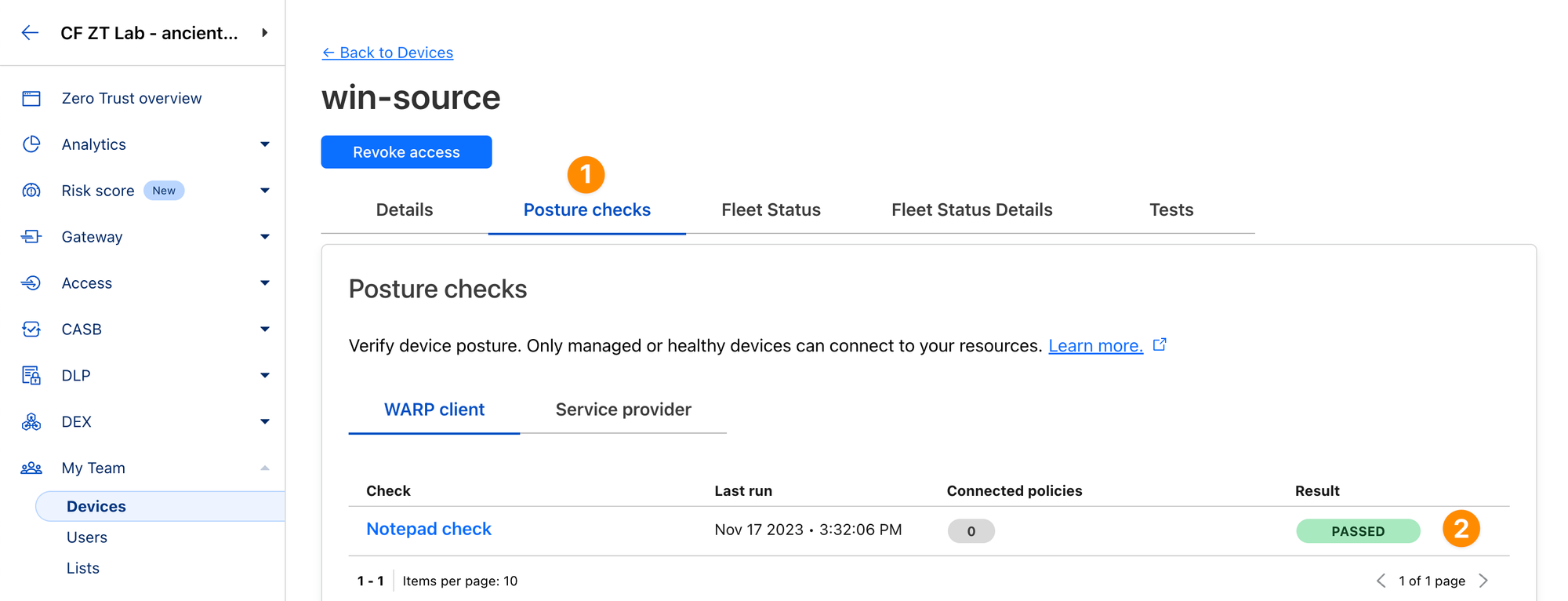
When Notepad is running, you should see the posture check as PASSED:
When you stop the Notepad, the posture check will change to FAILED in a few minutes (if it doesn't, double check in Task Manager that the notepad process isn't still running on the background):
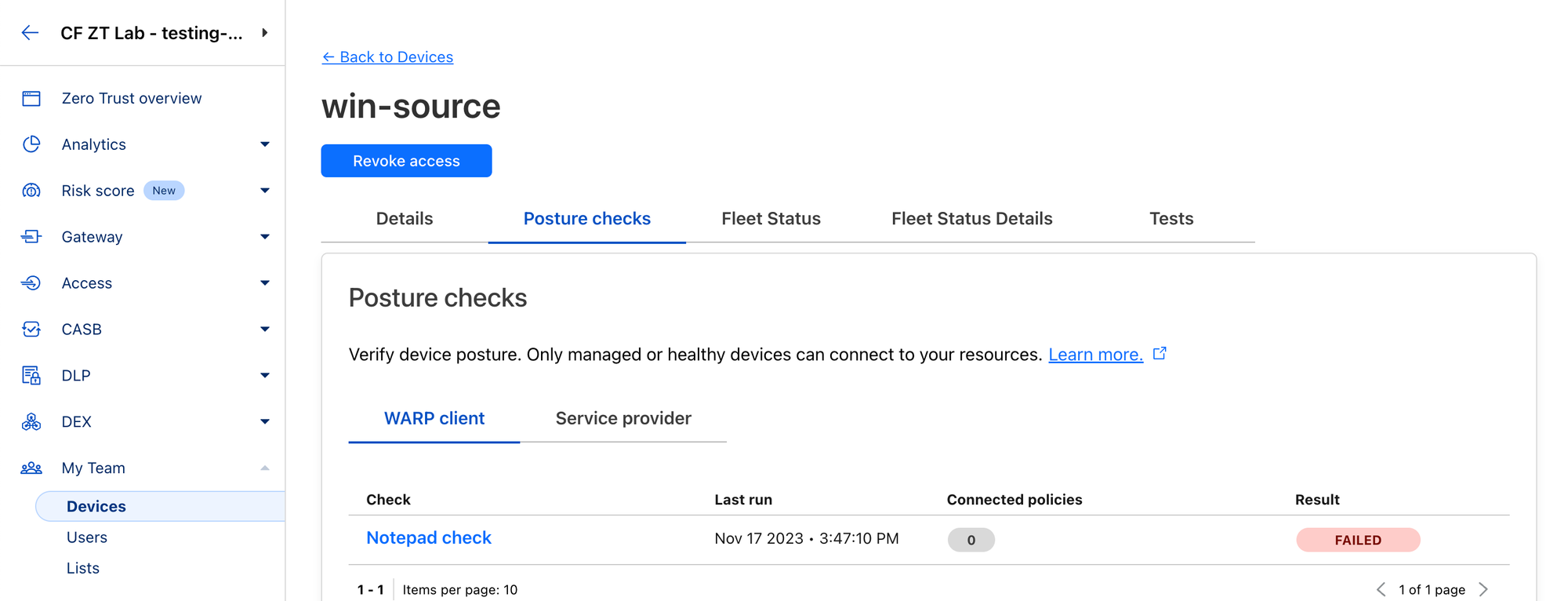
You can also see the history of posture activity of your whole team at Logs ‣ Posture.
Before continuing in the Zero Trust dashboard, review some troubleshooting features of the WARP client.
A vital aspect of troubleshooting WARP client issues is knowing how to guide a user to retrieve network logs - referred to as warp-diag output.
If you need to escalate WARP client issues to Cloudflare Support, warp-diag output will be required!warp-diag filewarp-diag output will appear on the desktop in zip format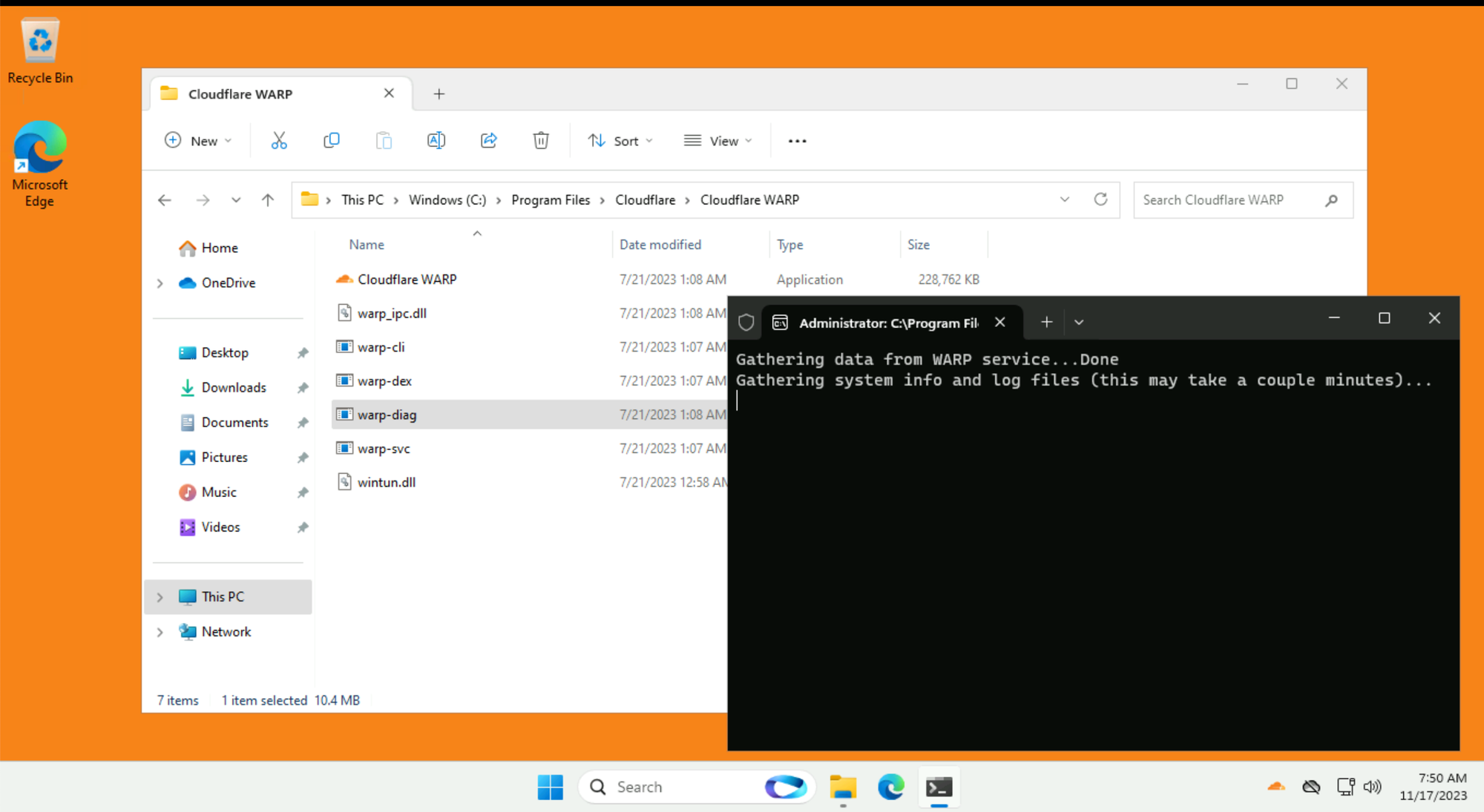
The steps to create WARP client logs for other operating systems are available here: How do I retrieve WARP Client Logs
The WARP client will try to run some connection tests.
engage.cloudflareclient.comconnectivity.cloudflareclient.comCan you open the warp-diag zip folder and identify the two connection tests?
Try to do this yourself, before proceeding below to the solution.
When you open the warp-diag folder you will see it contains several log and configuration files.
Some log files contain multiple iterations with a new number at the end:
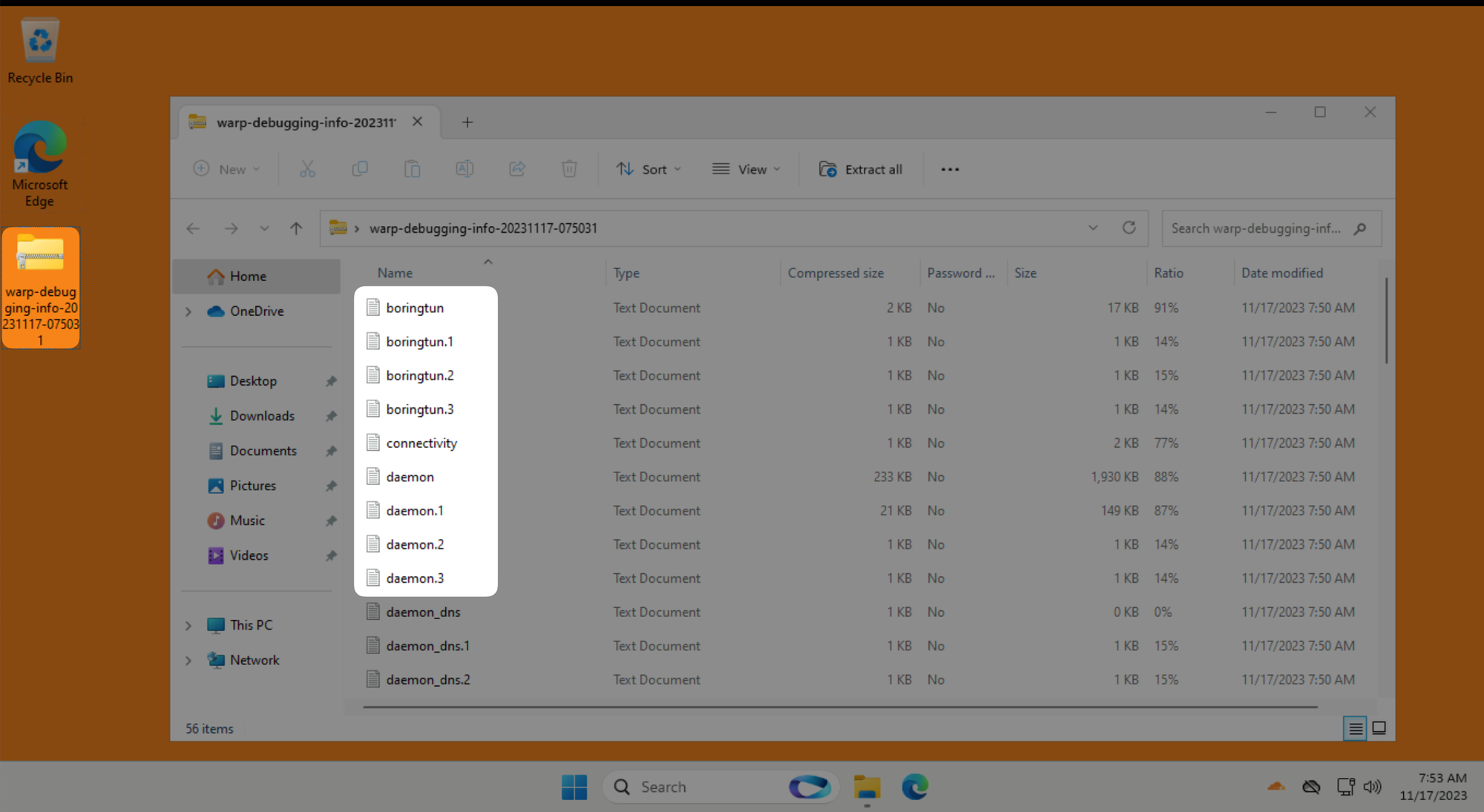
When warp-diag runs it breaks down longer time based logs into current day and previous days:
daemon.log ← The most current log. Todays events from the perspective of when warp-diag was rundaemon1.log ← Today -1 (aka yesterdays) events from the perspective of when warp-diag was runThe most useful is the daemon.log, it reads from the bottom upwards, the bottom most line is the most recent log entry.
Look for the most recent Initiate WARP Connection from when you started having issues:
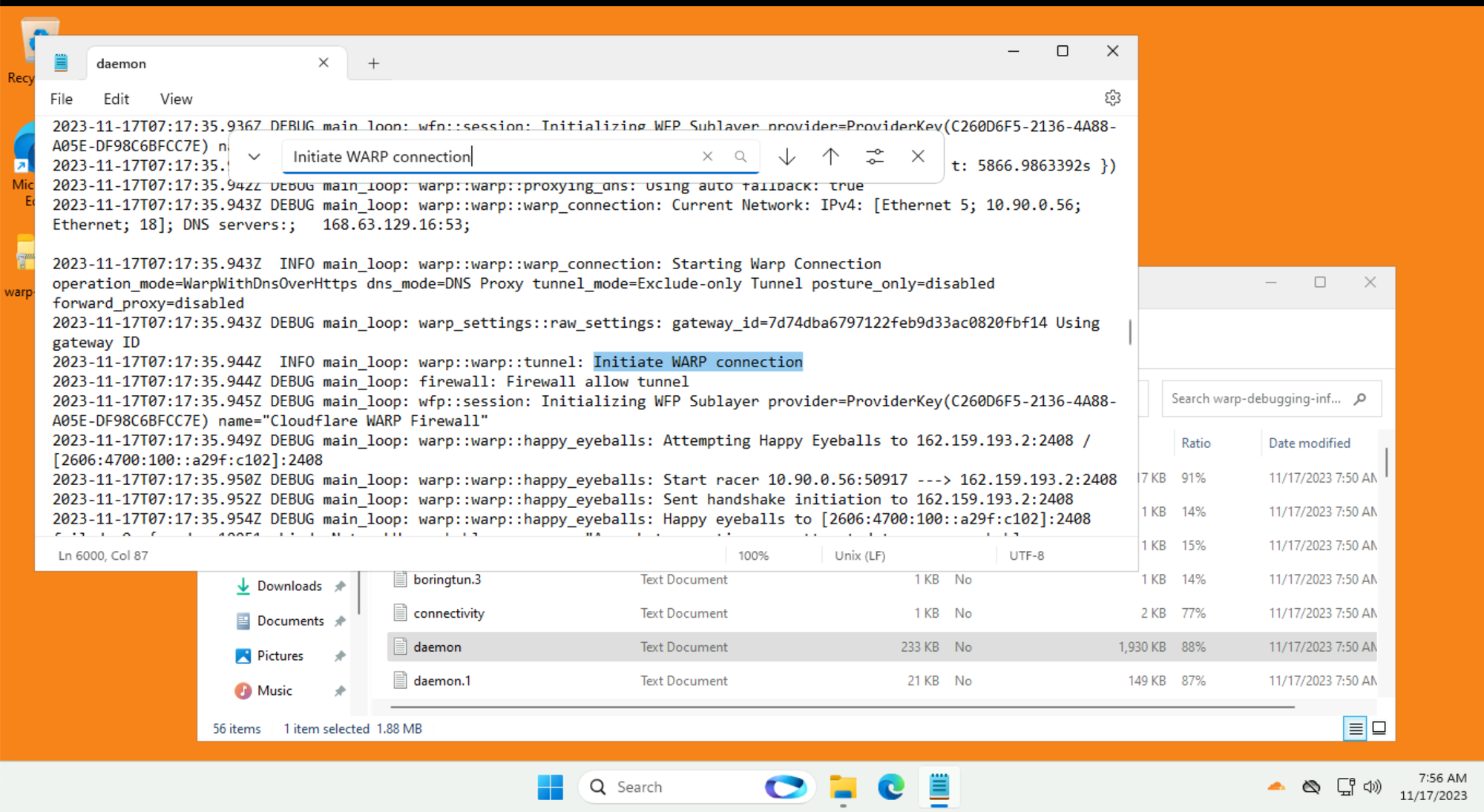
The WARP client will try to run some connection tests:
engage.cloudflareclient.com, it will show as warp/gateway=offconnectivity.cloudflareclient.com, it will show as warp/gateway=on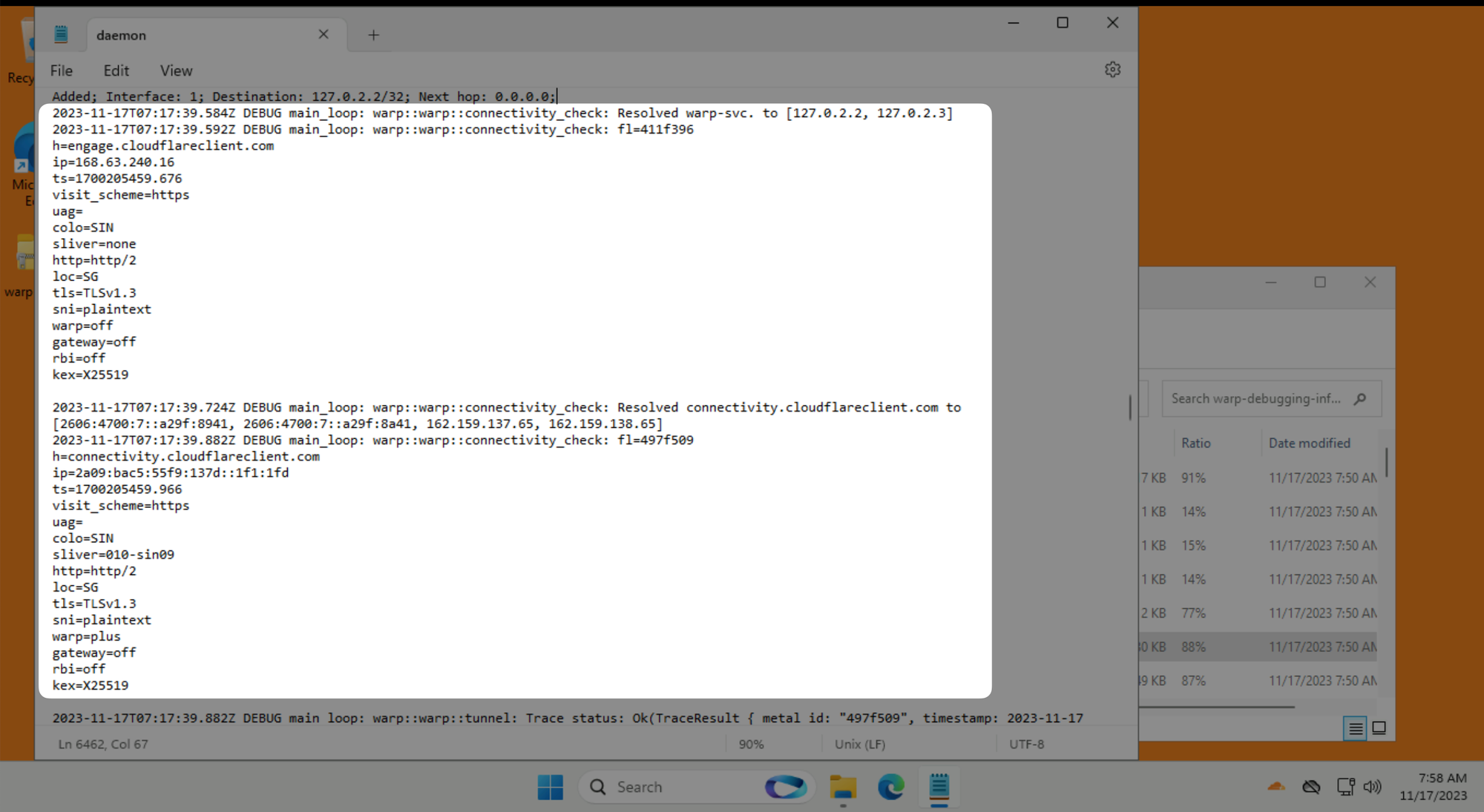
If the outside connection test fails, this is usually a problem with your internet connectivity.
If the internal connection test fails, check if there are any Network or HTTP policies that could be blocking the test before escalating to Cloudflare Support.