Workshop
- Identity provider
- WARP and device posture
- Cloudflare Tunnel
- Access and Private Network
- Browser isolation and App launcher
- Digital experience monitoring
Implement 3 types of Gateway policies:
⚙️ nocopy ⚙️
Selector: Application
Operator: in
Value: Video Streaming
Action: Block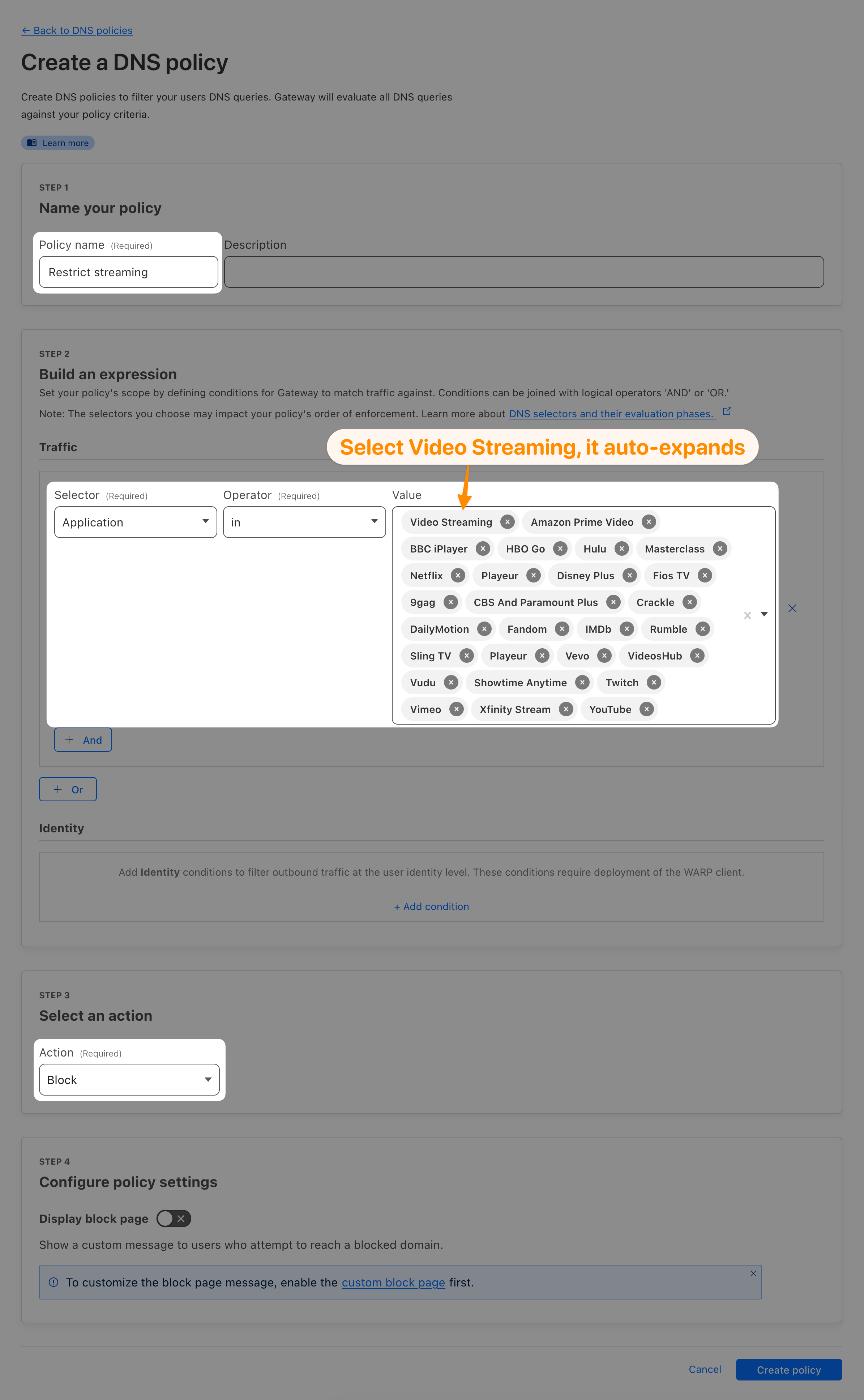
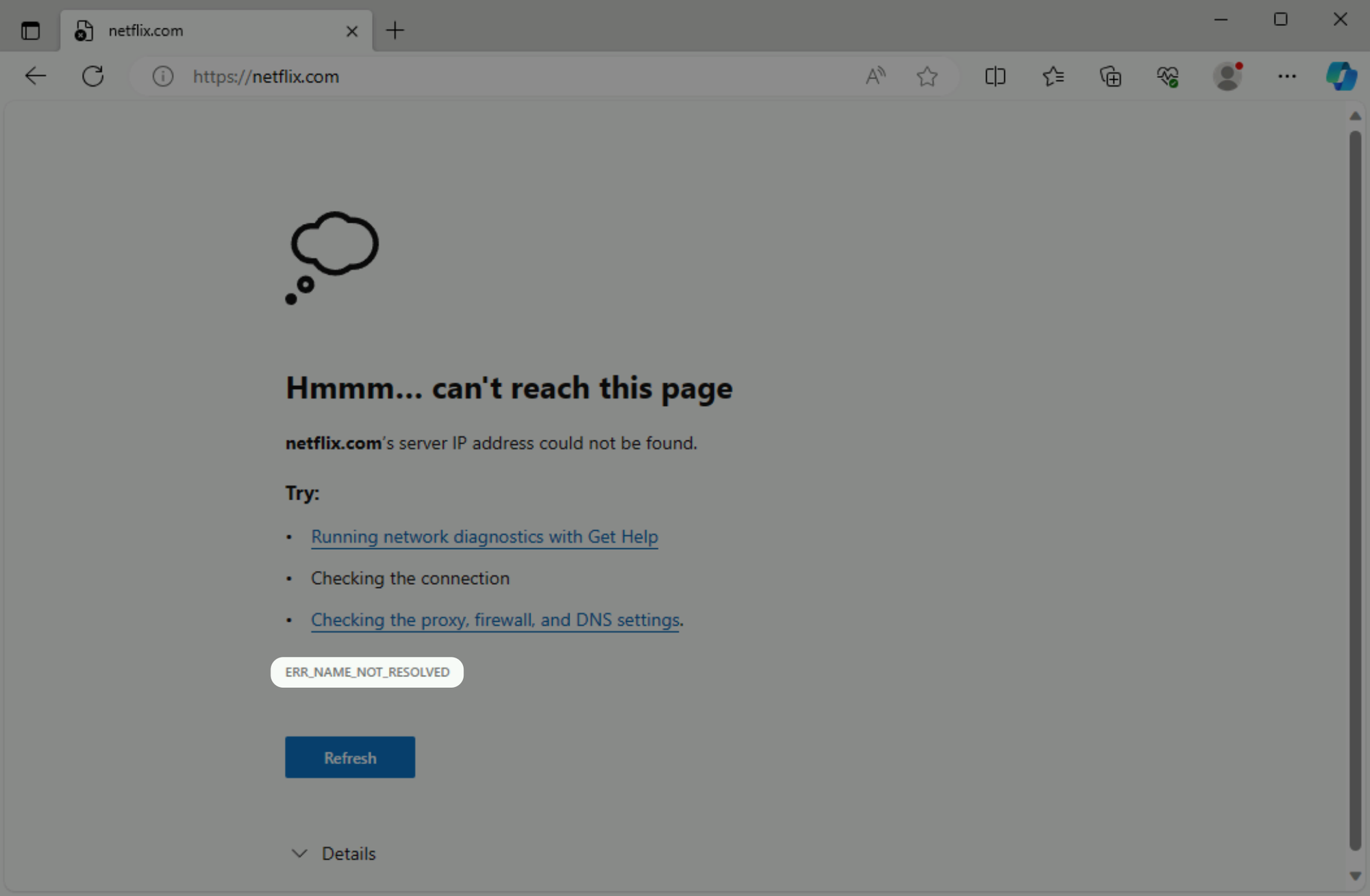
Try accessing netflix.com. You should receive a DNS_PROBE_FINISHED_NXOMAIN or ERR_NAME_NOT_RESOLVED error.
You have previously configured a Private Network Access Application, allowing direct access to your Linux server’s IP via WARP. This opened up access to all services on that server, including SSH.
ssh 10.x.x.x # Replace with your Linux server's IP[email protected]'s password:Let’s block access to SSH with a network policy.
⚙️ nocopy ⚙️
Selector: Destination IP
Operator: is
Value: <IP of your Linux server>
Selector: Destination Port
Operator: is
Value: 22
Action: Block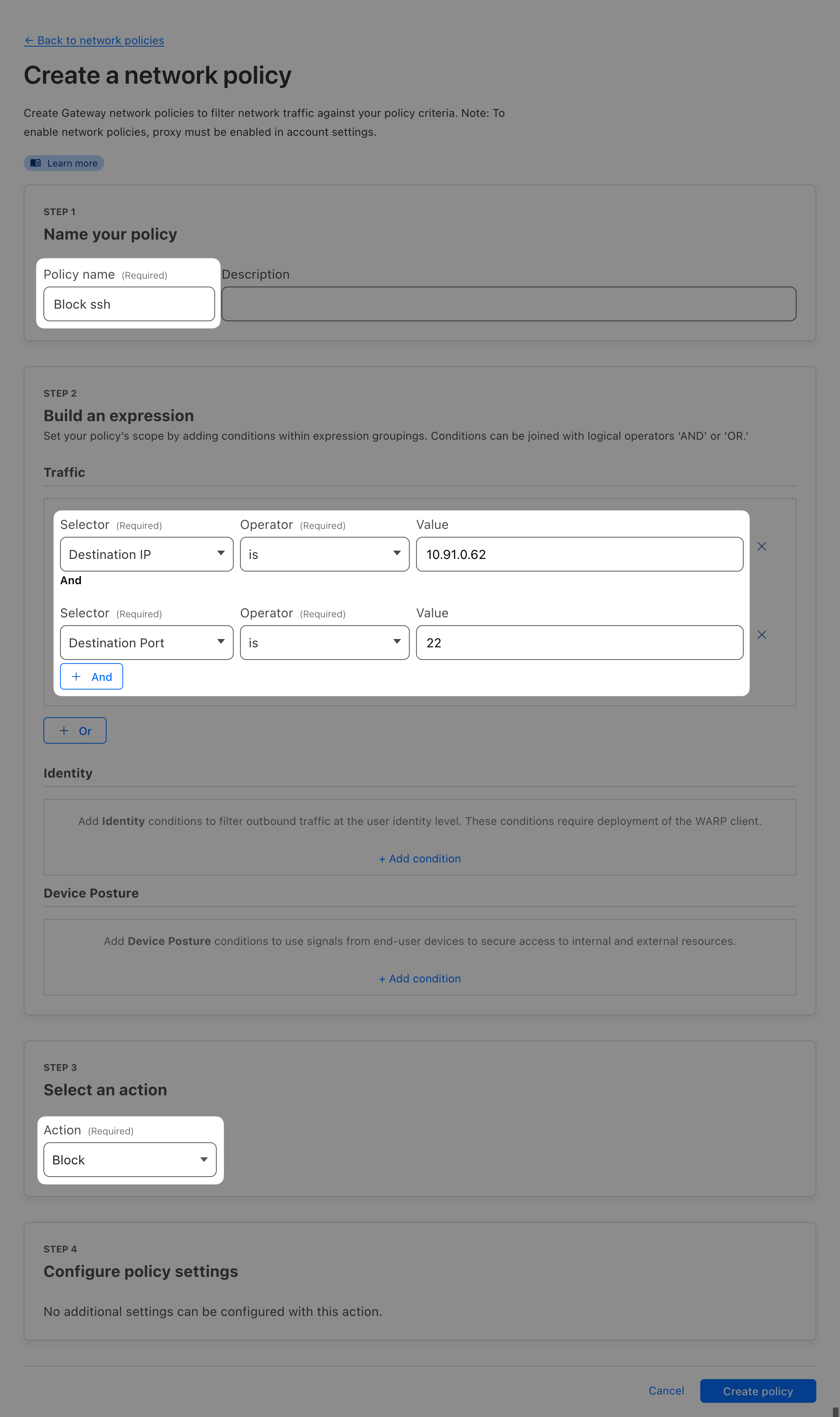
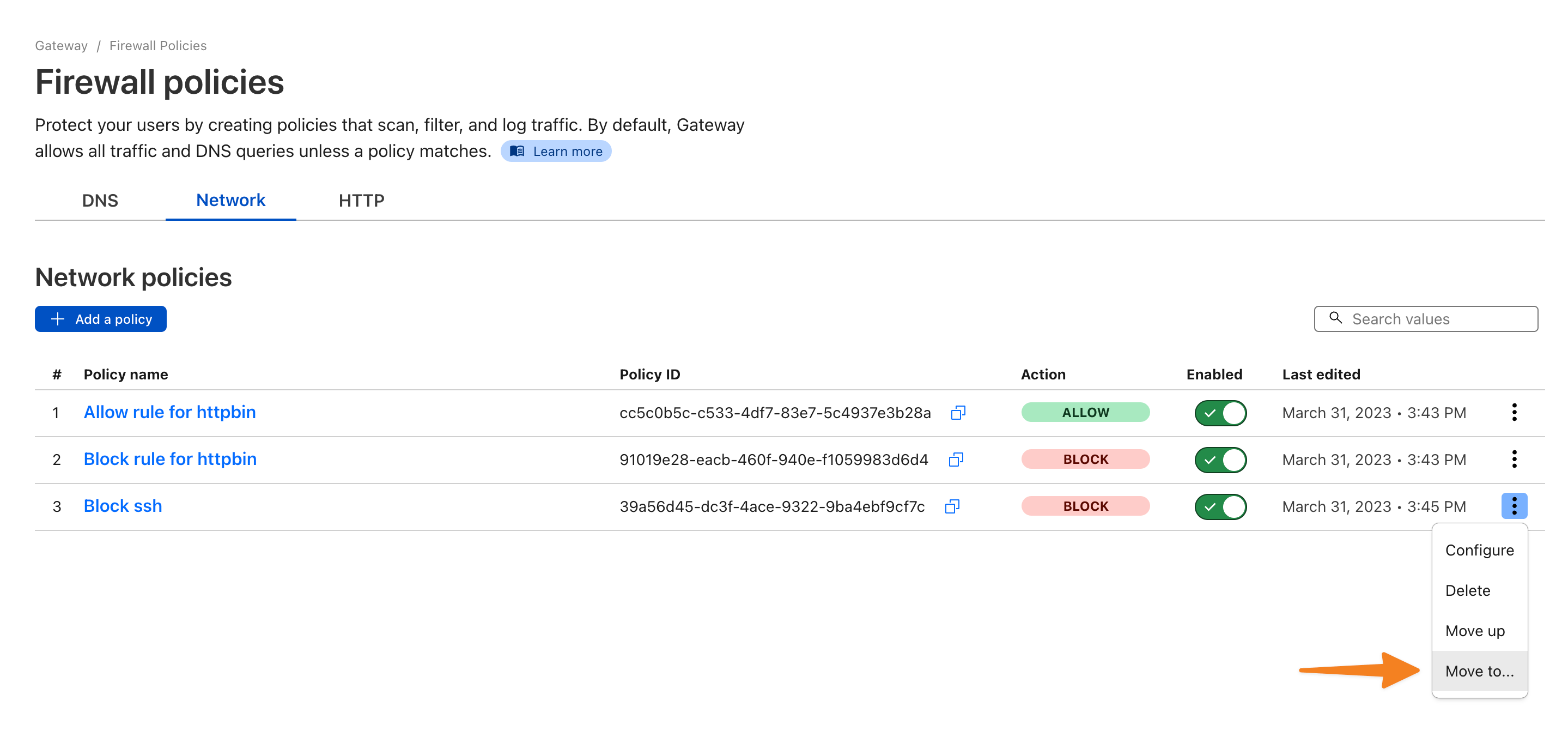
This will not work just yet. That’s because when you previously created the Private network Access Application, two default network policies were created for this IP. And since the policies are applied in the order they are defined, the default allow policy will take precedence over the block policy you just created.
With WARP on, try SSH to your origin server again. This time it should fail:
ssh 10.x.x.x # Replace with your Linux server's IPkex_exchange_identification: Connection closed by remote host
Connection closed by 10.x.x.x port 22Let’s now create a policy that will add an HTTP header to certain sites when accessed through Gateway. One use case for this is for example with Google Workspace where you can add X-Googapps-Allowed-Domains header with value of your domain. That will allow access to Google Workspace only for accounts from that specific domain (and block access to any personal accounts your users might have).
We have prepared a test site you can try this with: headers.cflr.workers.dev
⚙️ nocopy ⚙️
Selector: Domain
Operator: is
Value: headers.cflr.workers.dev
Action: AllowX-Custom-Header with some value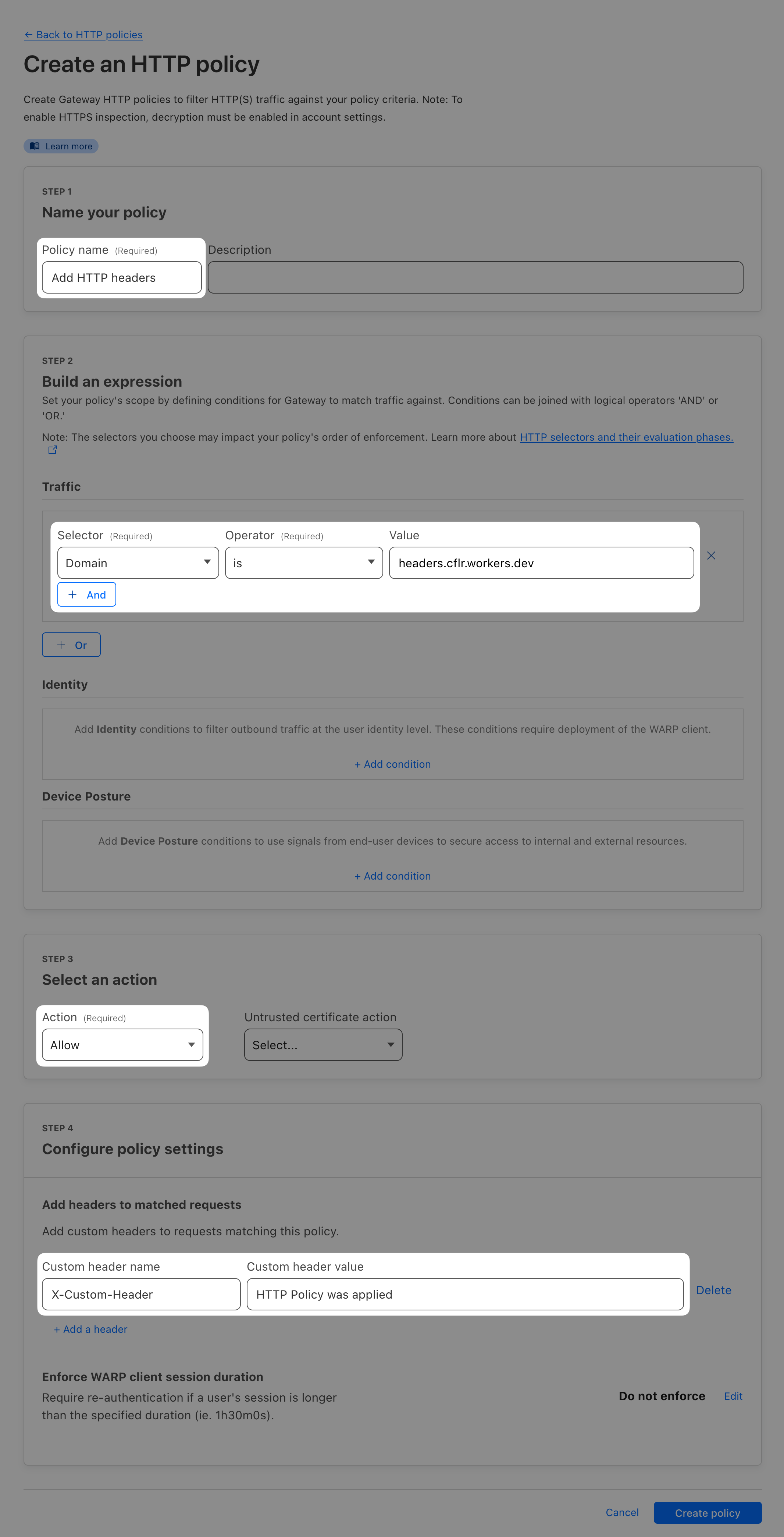
Try accessing headers.cflr.workers.dev with and without WARP turned on.
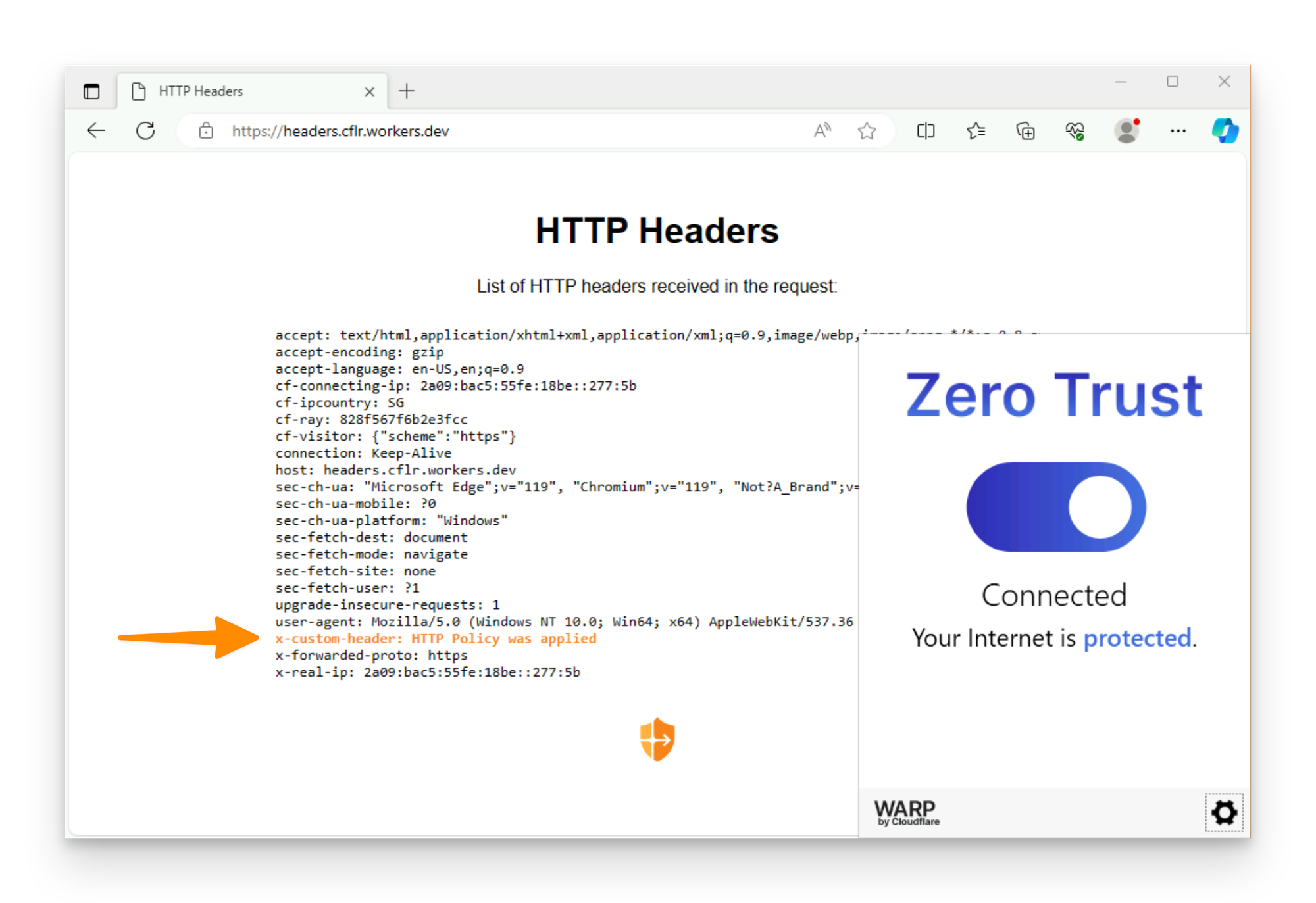
With WARP on, you should see your customer header added.